System monitoring
Presentation
Vulnerability-Lookup offers multiple methods for assessing system health, including monitoring key satellite components such as sighting tools, the email notification system, and data feeders.
Admin Panel
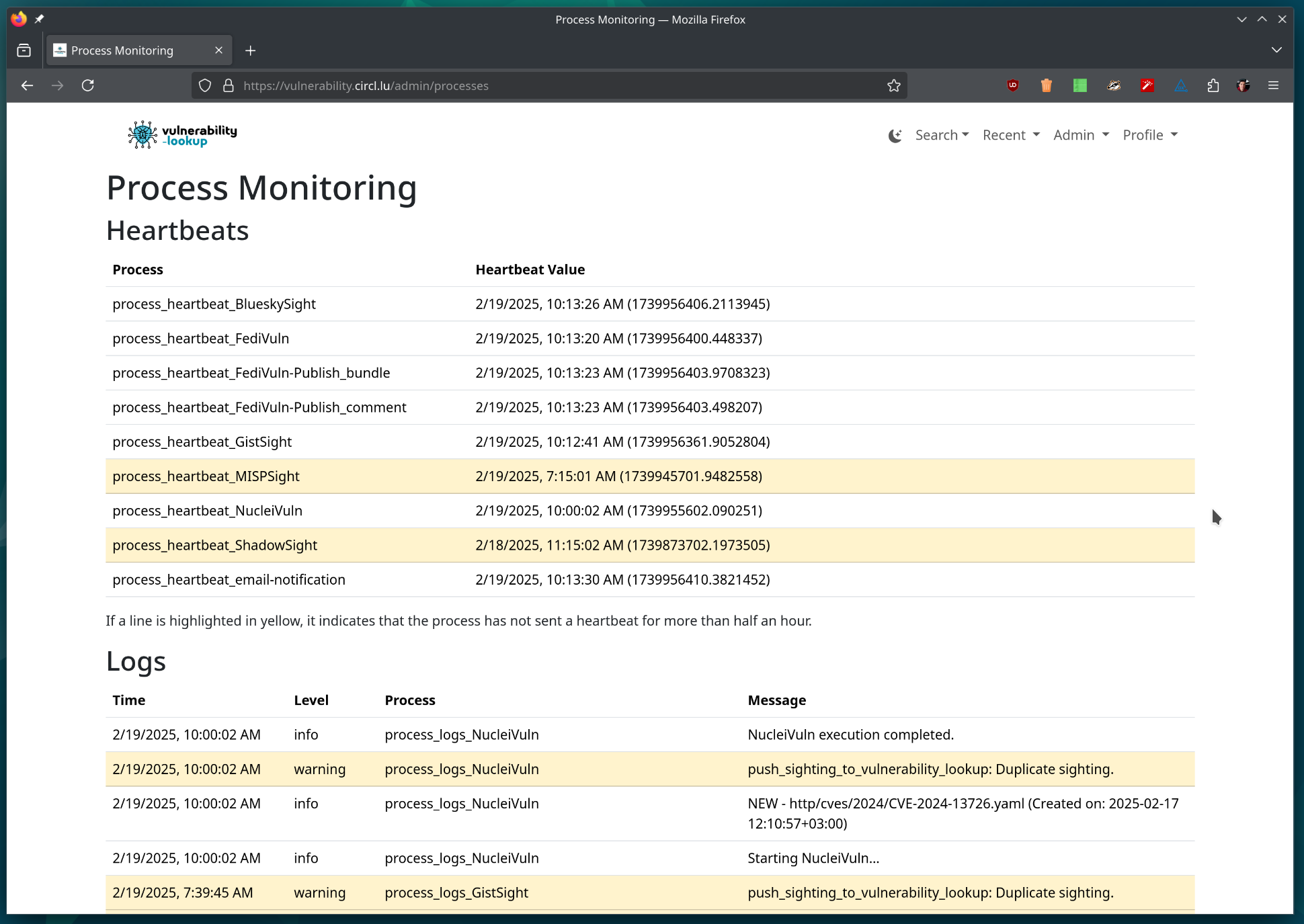
Processes heartbeat signals and logs
As shown in this example, the activity of all sighting tools is centralized in the Valkey keystore and displayed in the second table (Logs).
The primary goal of the first table (Heartbeats) is to detect abnormal states in any of the feeders.
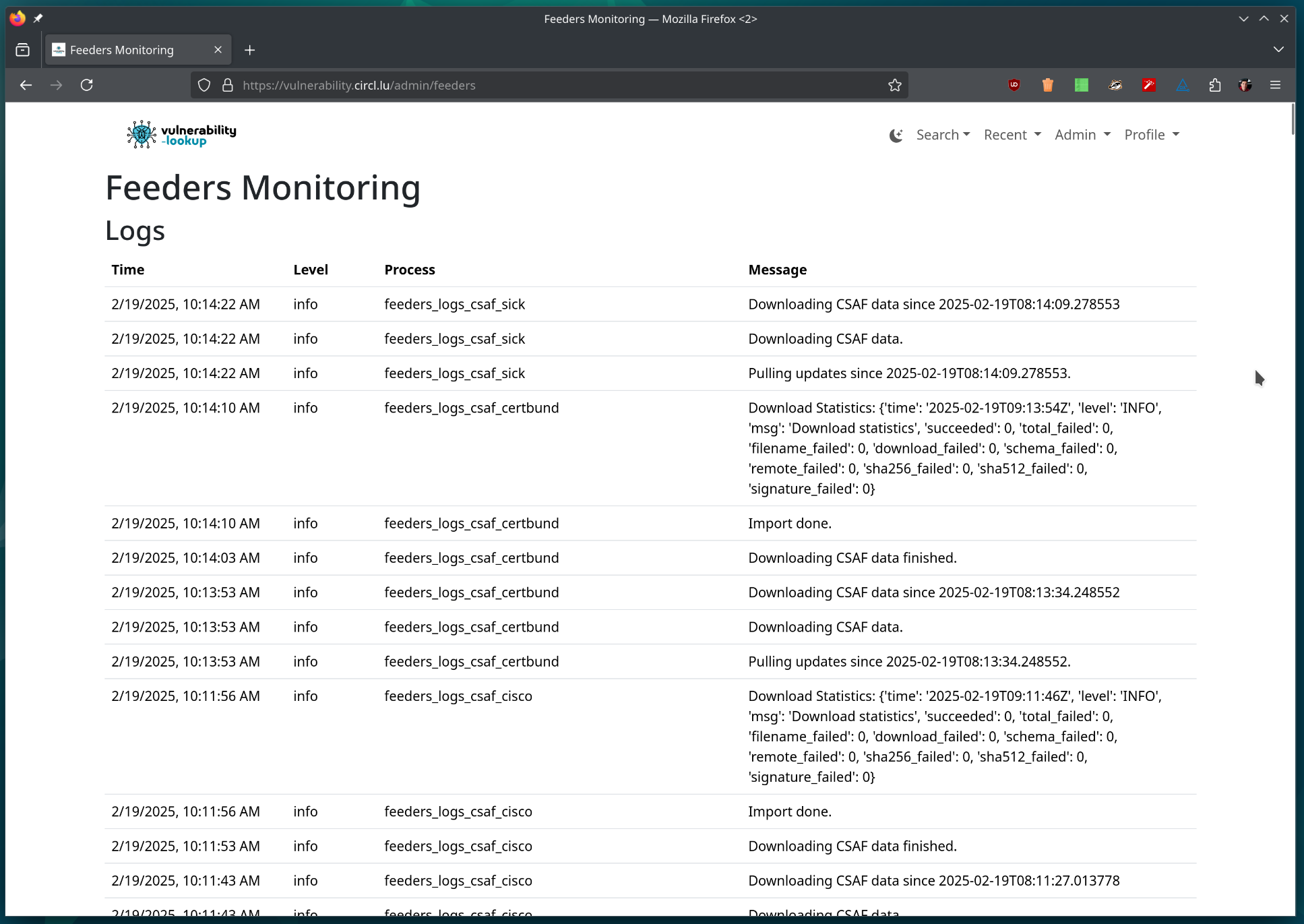
Feeders logs
API
Various endpoints for checking the system health are also provided through the API.
Examples:
$ curl https://vulnerability.circl.lu/api/system/redis_up
true
$ curl https://vulnerability.circl.lu/api/system/checkSMTP -H 'X-API-KEY: <YOUR-API-KEY>'
true
$ curl --silent https://vulnerability.circl.lu/api/system/checkProcess -H 'X-API-KEY: <YOUR-API-KEY>' | jq .
{
"process_heartbeat_BlueskySight": "2025-02-19T09:28:26.490720+00:00",
"process_heartbeat_FediVuln": "2025-02-19T09:28:20.458222+00:00",
"process_heartbeat_FediVuln-Publish_bundle": "2025-02-19T09:28:24.997171+00:00",
"process_heartbeat_FediVuln-Publish_comment": "2025-02-19T09:28:24.429215+00:00",
"process_heartbeat_GistSight": "2025-02-19T09:28:20.658896+00:00",
"process_heartbeat_MISPSight": "2025-02-19T09:15:02.327831+00:00",
"process_heartbeat_NucleiVuln": "2025-02-19T09:00:02.090251+00:00",
"process_heartbeat_ShadowSight": "2025-02-18T10:15:02.197351+00:00",
"process_heartbeat_email-notification": "2025-02-19T09:28:24.820832+00:00"
}Files
Each feeder has a dedicated log file, stored in the logs/ folder at the root of the project.
The configuration files for these log files can be found in:
vulnerabilitylookup/feeders/*_logging.json- or in
vulnerabilitylookup/feeders/<source>/
For example: vulnerabilitylookup/feeders/nvd_logging.json