Correlations
Presentation
Vulnerability-Lookup not only retrieves vulnerability information from various sources (such as NIST, PySec, and GitHub) but also connects related vulnerabilities, exploits, affected software, sightings, and other relevant metadata (Vulnrichment, CISA KEV).
Related vulnerabilities
Related vulnerabilities are located in the container vulnerability-lookup:linked.
$ curl --silent 'https://vulnerability.circl.lu/api/vulnerability/CVE-2015-2051?with_linked=true' | jq 'keys'
[
"containers",
"cveMetadata",
"dataType",
"dataVersion",
"vulnerability-lookup:linked"
]The correlations are derived from the various sources utilized by the Vulnerability-Lookup installation:
$ curl --silent 'https://vulnerability.circl.lu/api/vulnerability/CVE-2015-2051?with_linked=true' | jq '.["vulnerability-lookup:linked"] | keys'
[
"fkie_nvd",
"github",
"gsd",
"variot"
]You can easily get related vulnerabilities from a specific source:
$ curl --silent 'https://vulnerability.circl.lu/api/vulnerability/CVE-2015-2051?with_linked=true' | jq '.["vulnerability-lookup:linked"]["github"]'
[
[
"ghsa-x629-5xff-w7qg",
{
"schema_version": "1.4.0",
"id": "GHSA-x629-5xff-w7qg",
"modified": "2025-01-06T15:30:58Z",
"published": "2022-05-17T03:11:58Z",
"aliases": [
"CVE-2015-2051"
],
"details": "The D-Link DIR-645 Wired/Wireless Router Rev. Ax with firmware 1.04b12 and earlier allows remote attackers to execute arbitrary commands via a GetDeviceSettings action to the HNAP interface.",
"severity": [
{
"type": "CVSS_V3",
"score": "CVSS:3.1/AV:A/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H"
}
],
"affected": [],
"references": [
{
"type": "ADVISORY",
"url": "https://nvd.nist.gov/vuln/detail/CVE-2015-2051"
},
{
"type": "WEB",
"url": "https://supportannouncement.us.dlink.com/announcement/publication.aspx?name=SAP10282"
},
{
"type": "WEB",
"url": "https://www.exploit-db.com/exploits/37171"
},
{
"type": "WEB",
"url": "http://securityadvisories.dlink.com/security/publication.aspx?name=SAP10051"
},
{
"type": "WEB",
"url": "http://www.securityfocus.com/bid/72623"
},
{
"type": "WEB",
"url": "http://www.securityfocus.com/bid/74870"
}
],
"database_specific": {
"cwe_ids": [
"CWE-77"
],
"severity": "HIGH",
"github_reviewed": false,
"github_reviewed_at": null,
"nvd_published_at": "2015-02-23T17:59:00Z"
}
}
]
]Sightings
An other way to correlate vulnerabilities is to use the sightings.
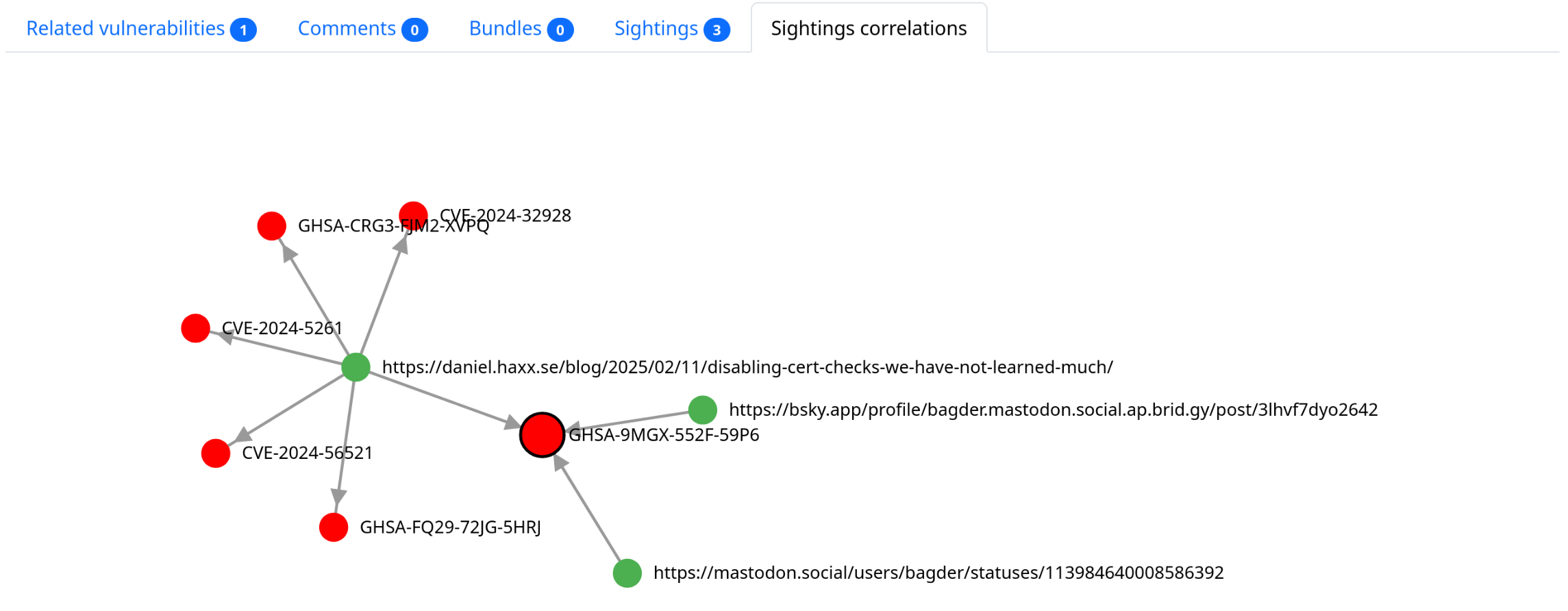
Correlations for CVE-2024-5261
You can explore the relationships between sightings and vulnerabilities through the graphical interface or by using the API as explained in the next section.
Retrieving vulnerability sightings
$ curl --silent 'https://vulnerability.circl.lu/api/vulnerability/CVE-2024-5261?with_sightings=true' | jq '.["vulnerability-lookup:sightings"]'
[
{
"uuid": "eec2c8fd-f664-4e73-b3f5-651db5fa4f3f",
"vulnerability_lookup_origin": "1a89b78e-f703-45f3-bb86-59eb712668bd",
"author": "9f56dd64-161d-43a6-b9c3-555944290a09",
"vulnerability": "cve-2024-5261",
"type": "seen",
"source": "https://mastodon.social/users/bagder/statuses/113984646246260950",
"creation_timestamp": "2025-02-11T09:54:37.066650Z"
},
{
"uuid": "6de72384-c623-4e70-bd38-1040c4e29bab",
"vulnerability_lookup_origin": "1a89b78e-f703-45f3-bb86-59eb712668bd",
"author": "9f56dd64-161d-43a6-b9c3-555944290a09",
"vulnerability": "cve-2024-5261",
"type": "seen",
"source": "https://bsky.app/profile/bagder.mastodon.social.ap.brid.gy/post/3lhvfc2enwhl2",
"creation_timestamp": "2025-02-11T10:04:50.326511Z"
},
{
"uuid": "61f4c902-4258-423a-929a-4b473e3d16a0",
"vulnerability_lookup_origin": "1a89b78e-f703-45f3-bb86-59eb712668bd",
"author": "9f56dd64-161d-43a6-b9c3-555944290a09",
"vulnerability": "CVE-2024-5261",
"type": "seen",
"source": "https://daniel.haxx.se/blog/2025/02/11/disabling-cert-checks-we-have-not-learned-much/",
"creation_timestamp": "2025-02-11T14:00:07.000000Z"
}
]Finding correlations with other vulnerabilities
$ curl --silent 'https://vulnerability.circl.lu/api/sighting/?source=https://daniel.haxx.se/blog/2025/02/11/disabling-cert-checks-we-have-not-learned-much/' | jq '.data[].vulnerability'
"GHSA-fq29-72jg-5hrj"
"CVE-2024-32928"
"GHSA-9mgx-552f-59p6"
"CVE-2024-56521"
"GHSA-crg3-fjm2-xvpq"
"CVE-2024-5261"$ curl --silent 'https://vulnerability.circl.lu/api/vulnerability/CVE-2024-32928?with_linked=true' | jq '.["vulnerability-lookup:linked"]["github"]'
[
[
"ghsa-fq29-72jg-5hrj",
{
"schema_version": "1.4.0",
"id": "GHSA-fq29-72jg-5hrj",
"modified": "2024-08-20T18:31:21Z",
"published": "2024-08-19T18:32:07Z",
"aliases": [
"CVE-2024-32928"
],
"details": "The libcurl CURLOPT_SSL_VERIFYPEER option was disabled on a subset of requests made by Nest production devices which enabled a potential man-in-the-middle attack on requests to Google cloud services by any host the traffic was routed through.",
"severity": [
{
"type": "CVSS_V3",
"score": "CVSS:3.1/AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:N/A:N"
}
],
"affected": [],
"references": [
{
"type": "ADVISORY",
"url": "https://nvd.nist.gov/vuln/detail/CVE-2024-32928"
},
{
"type": "WEB",
"url": "https://support.google.com/product-documentation/answer/14771247?hl=en&ref_topic=12974021&sjid=9111851316942032590-NA#zippy="
}
],
"database_specific": {
"cwe_ids": [],
"severity": "MODERATE",
"github_reviewed": false,
"github_reviewed_at": null,
"nvd_published_at": "2024-08-19T17:15:07Z"
}
}
]
]